

My HDMI tops out at 144hz, issue still present.


My HDMI tops out at 144hz, issue still present.


1440p at 170Hz with the DisplayPort. But I also tried going down to 60hz, but in that brief time I did that, that made the flickering issue even more apparent.
I hear that Gnome can struggle on touchscreens due to some GTK bugginess.
Plasma is probably a good bet since it has a dedicated touch friendly mode and is tested on the Steam Deck, which has a touch screen.
There’s third party Appimages. They also had a blog post discussing using Appimages for testing builds. If that gets done, I don’t see why they wouldn’t offer an official build.


I believe it’s an Apple Silicon limitation in their lower end chips.


On iOS, I feel like doing things take a few extra taps and swipes than they would on Android.
But on the whole apps made for iOS feel higher quality. Even Google’s own apps are better on iOS. I feel like the problem is that Apple forces developers to adopt changes quickly, whereas Google lets apps use years old API versions.


Makes sense that it includes snap given that KDE officially supports their apps packaged as snaps, unlike Gnome.
If I recall correctly, aren’t they going for an Arch base? I assume they’re going to be enabling AppArmor so that the snap sandboxing is mostly working, except for the patches Canonical have failed to upstream so far.


I’m tempted by this too (or maybe the upcoming MacBook Air). I’m just worried that I’m not going to like MacOS. I’m pretty happy with Linux, like FOSS, but Apple just has the best hardware at the moment.


Nope, both on the same Wifi network. Can’t think of why it would be showing differently. Not even force refreshing the page did anything. But I just checked again and now it’s showing the right prices.


Huh
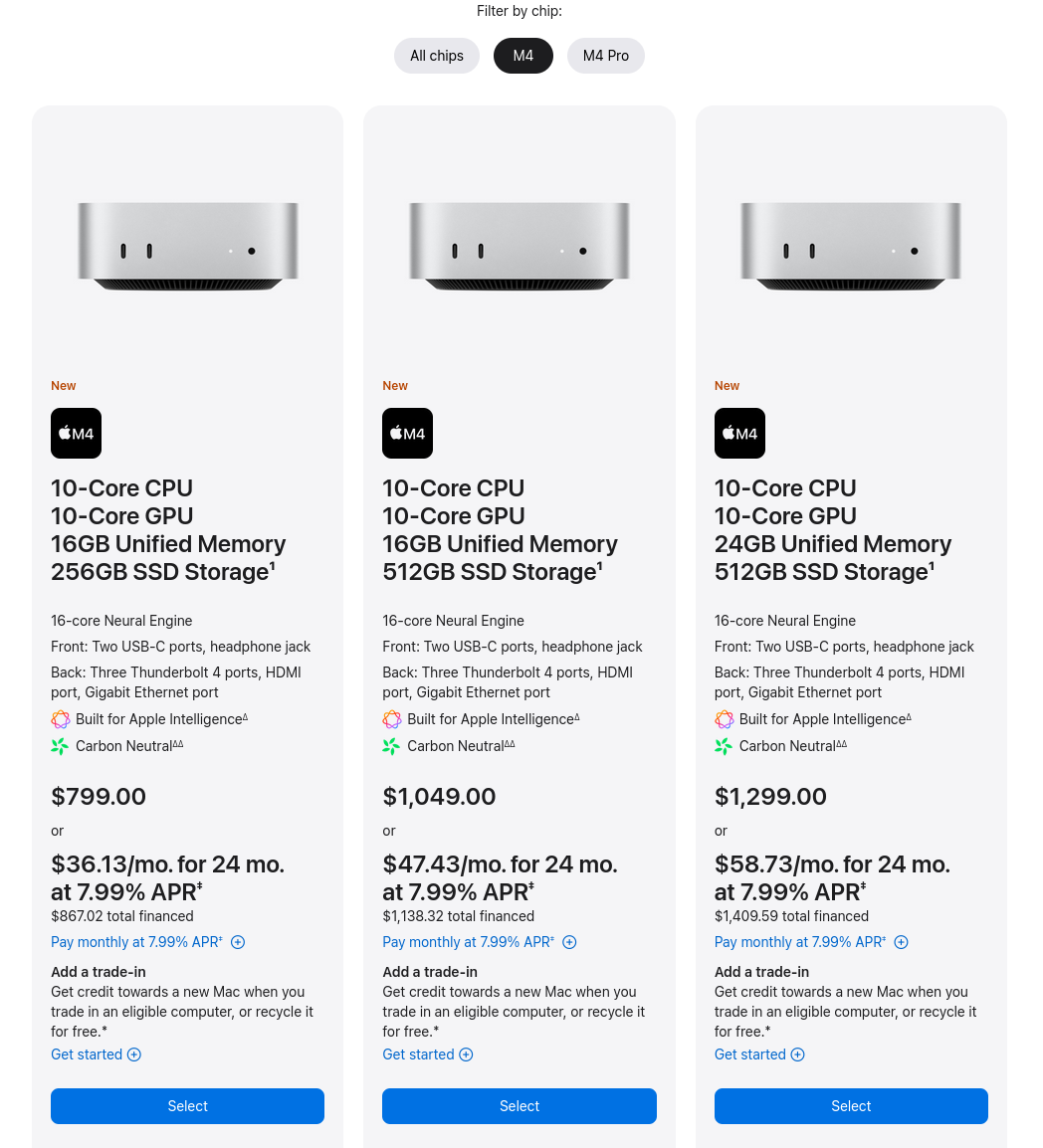
It shows up as $599 on my iPhone, but not desktop.


Lowest I’m seeing from the preorder screen is $799.


$200 base price increase, ouch.
Edit: apparently it starts at $599, but for some reason Apple is showing me $799 for the base model.


Fair enough. It certainly benefits Apple if people with full photo libraries instead move those to iCloud with costly subscriptions.


Honestly doesn’t bother me that much, especially on a desktop. I have a large external hard drive for mass storage and an USB dongle that connects to an NVME drive.
Right now I’m using a desktop with Linux on it, but I’ve been debating replacing my desktop with a Mac (maybe MacBook or Mac Mini). I’d be fine with the small storage, what was really concerning me was the 8GB starting RAM and $200 upgrade to 16GB.


Thankfully, the base model now has 16GB of RAM.
Drew started the project but he isn’t really involved anymore. Simon Ser is the lead maintainer now.
Note that this article is from 2022, albeit with an update in 2024.
I was confused when they mentioned they upgraded from Debian bullseye, were using an old Firefox version, and had to explicitly enable Wayland for Firefox. I then saw the date of the post.


With 2024.10, Bitwarden could no longer be built without their proprietary SDK.
That was deemed a bug and now the SDK is also licensed under the GPL.


Hopefully with 16GB of RAM at the same starting price.
Brand new Mac Mini, just came out today. It has a full year of warranty left.