Considering how most of the Internet is encrypted with TLS, if you add DNSSEC+DoH/DoT on top, trying to MITM someone on a public WiFi is way harder than it was, unless you’re a state-level adversary and you’re able to craft valid certificate for a domain you don’t control from a globally trusted (root) certificate autority (which will lose its trusted status quite fast once discovered, ex: CNNIC)
Yeah, the days of your local coffee shops Wi-Fi being a problem or mostly gone. Not the VPN doesn’t have a place anymore though. If you’re trying to hide your downloading of ISOs from your ISP it’s still a perfectly reasonable method. Or temporarily relocating yourself to another country to make a purchase or watch some streaming content both perfectly reasonable.
Of course some of the streaming providers are getting wise to this.
I have a VPN so I can securely access my home network when I’m away
Yeah, pptp will always have a strong purpose and home. I’m more speaking to the viability of commercial anonymization VPN.
I have a feeling you are using pptp as shorthand for Point to Point disregarding protocol and already knows what I’m about to say. To anyone else reading this - PPTP is obsolete and unsafe. Use an alternative such as OpenVPN, WireGuard or SSTP.
Tailscale FTW. I honestly haven’t looked at the underlying protocols in years. Was using ubiquiti’s implementation of openVPN but it seemed to get grumpy when you connect one user multiple times.
Poking around at available products, I had settled on zero tier and tailscale, I went ahead and tried tail scalefirst because it was basically free for my house. One month in, I had a few decent detectable guys at work join me on a trial there. Full licenses for everybody at work cost less than my Cisco refresh. And makes it so that the office is no longer a critical hosting site.
OpenVPN allows multiple connections if you enable duplicate-cn:
–duplicate-cn
Allow multiple clients with the same common name to concurrently connect.
In the absence of this option, OpenVPN will disconnect a client instance upon connection of a new client having the same common name.
https://openvpn.net/community-resources/reference-manual-for-openvpn-2-4/There’s also headscale if you wanna selfhost the tailscale control server:
https://github.com/juanfont/headscaleIt was allowing me to make multiple connections but they were unpredictable, I assumed it was a unifi problem back in the day thanks for the information!
That’s not what these commercial VPNs are for.
I use a VPN for the same reason I use the Internet. Porn.
why would I need to hide my terabytes of Linux ISO downloads?
Bill Gates, man, Bill Gates
It’s all fun and games until a Microsoft Purity Enforcement squad is kicking in your door.
Nah, it’s all good I subscribe to Linus Torvalds protection services. When the Microsoft vans get within four blocks of my address, They’ll drop ship in dozens of fully-armed penguin paratroopers. After the incursion they even send in a penguin based cleaner team to help get rid of the remains.
Because we see which distros you’re using, and we judge you for it.
Gentoo, in 2024? Really? You should be using Arch if that’s your thing. It’s not the 90s any more.
Arch? I prefer EndeavorOS as it lets me easily install an arch distro using a nice GUi, I really don’t care about the nitty gritty of setting up my own network manually, i am like 99.9% of people in that regard
You don’t want their admin to contact you about how you’re a n00b for not using Arch.
Or the tld is .mobi
Interesting read, thanks!
Not all applications on your computer may be encrypting their packet traffic properly, though. That goes especially for the applications that might be trying to reach out for resources on your local home network (like printers, file shares, and other home servers) as well as DNS requests which are usually still made in the open. I would not recommend eschewing an entire security layer willy-nilly like that. On public Wi-Fi, I would definitely still suggest either a VPN or using your cell phone as a tether or secure hotspot instead if possible.
Sure, but it’s also like, if you’re stepping away from your laptop for a few minutes should you lock the screen or shut it down completely.
The most secure option is to shut it down completely, but also it’s fine to just lock your screen.
If you’ve already got a VPN and it’s as easy as locking your screen to enable, go for it, use it. But if you don’t, you don’t need to go out and get one. You’ll generally be ok without one.
The most secure option is bringing the laptop with you.
I mean, technically - the most secure option is irrevocably destroying the laptop everytime you have a break.
Oh so a one time pad
The most secure & economical option is to never go outside
As a network security expert, I’ve got that on LOCK
I’m not online enough to understand this.
how do I reboot my computer?
Throw a brick at it.
That’s just turning it off with Style✨
that’s gonna brick it. it’s right there in its name.
people on the internet and their advice sometimes, ffs.
Nah, you just gotta do it correctly, yeah you might brick a few computers, TVs, cars or a couple electrical mains boxes, but once you master the technique you’ll be able to restart anything.
We call that percussive maintenance… the brick is optional.
Hailey “Hawk Tuah” Welch is an influencer that gained a lot of popularity from her nickname (the sound of spitting, with HEAVY implications of performing fellacio). She used her platform to voice a very reasonable and intelligent opinion, which surprised a lot of people because her nickname is essentially blowjob queen.
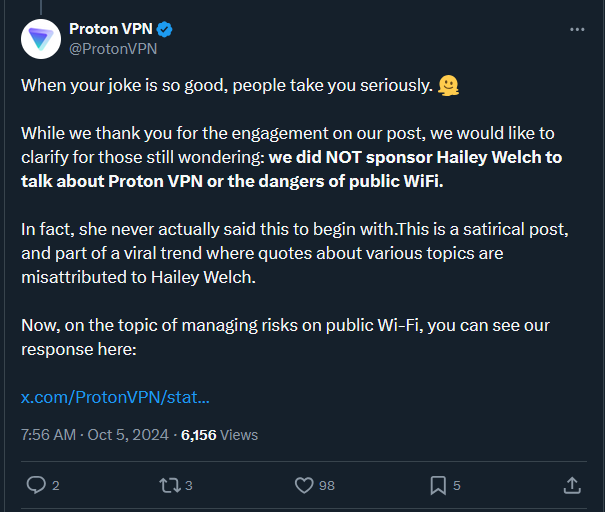
One of her opinions is that it’s important to spread cyber security and used her fame to try to educate the public (potentially a fake story from the image? Idk this drama). And some xit-head claiming to be a cyber security expert ate the onion and offered some shitty advice. Proton fact checked them, because there are a ton of fake news stories about her right now.
Hailey “Hawk Tuah” Welch is an influencer
Ah, OK, I’m out.
Thanks for clarifying. This thread has felt like the cyber security equivalent of the Flat Earth Theory.
Sorry, not just implication; she was straight up talking about that.
deleted by creator
Popular format
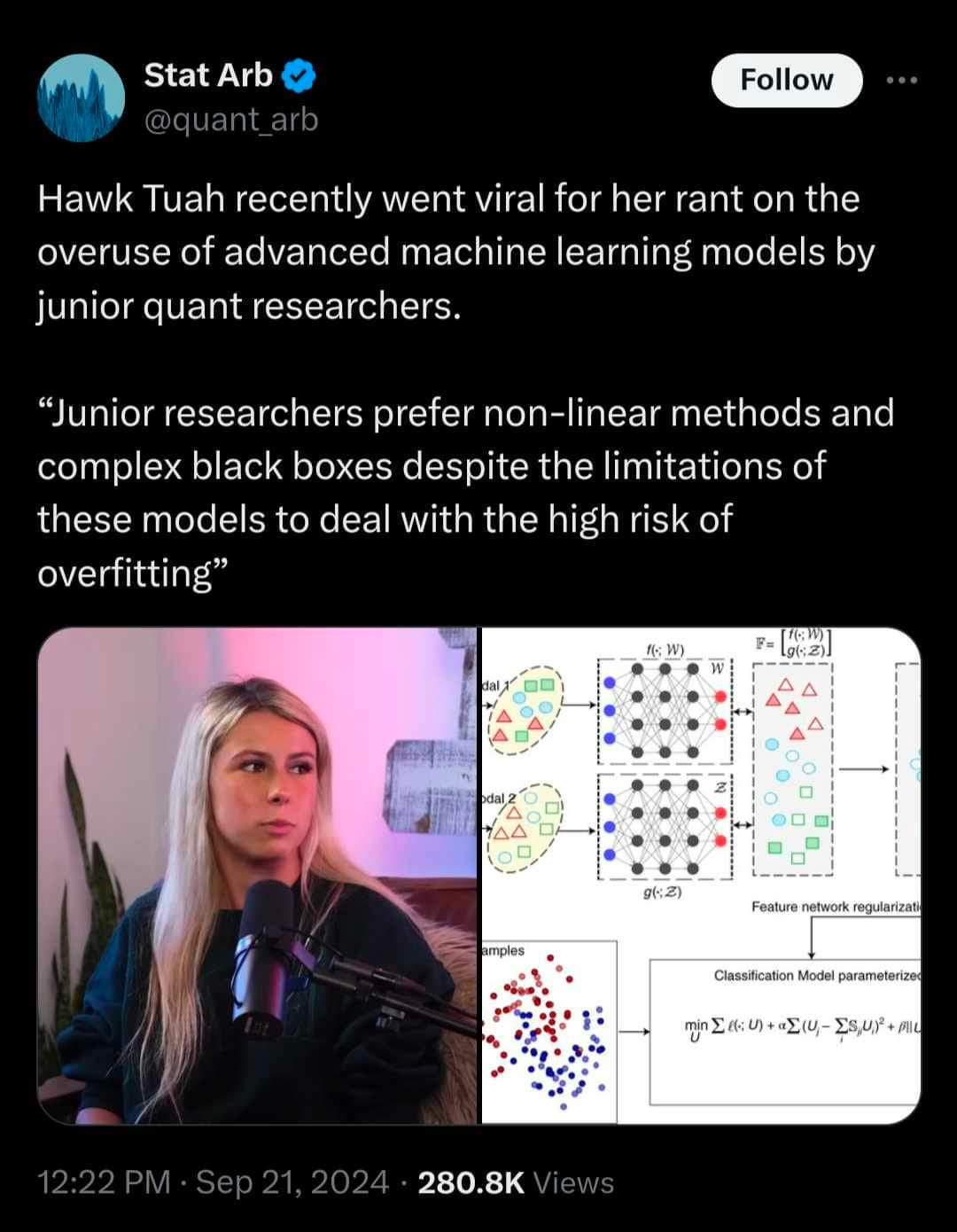
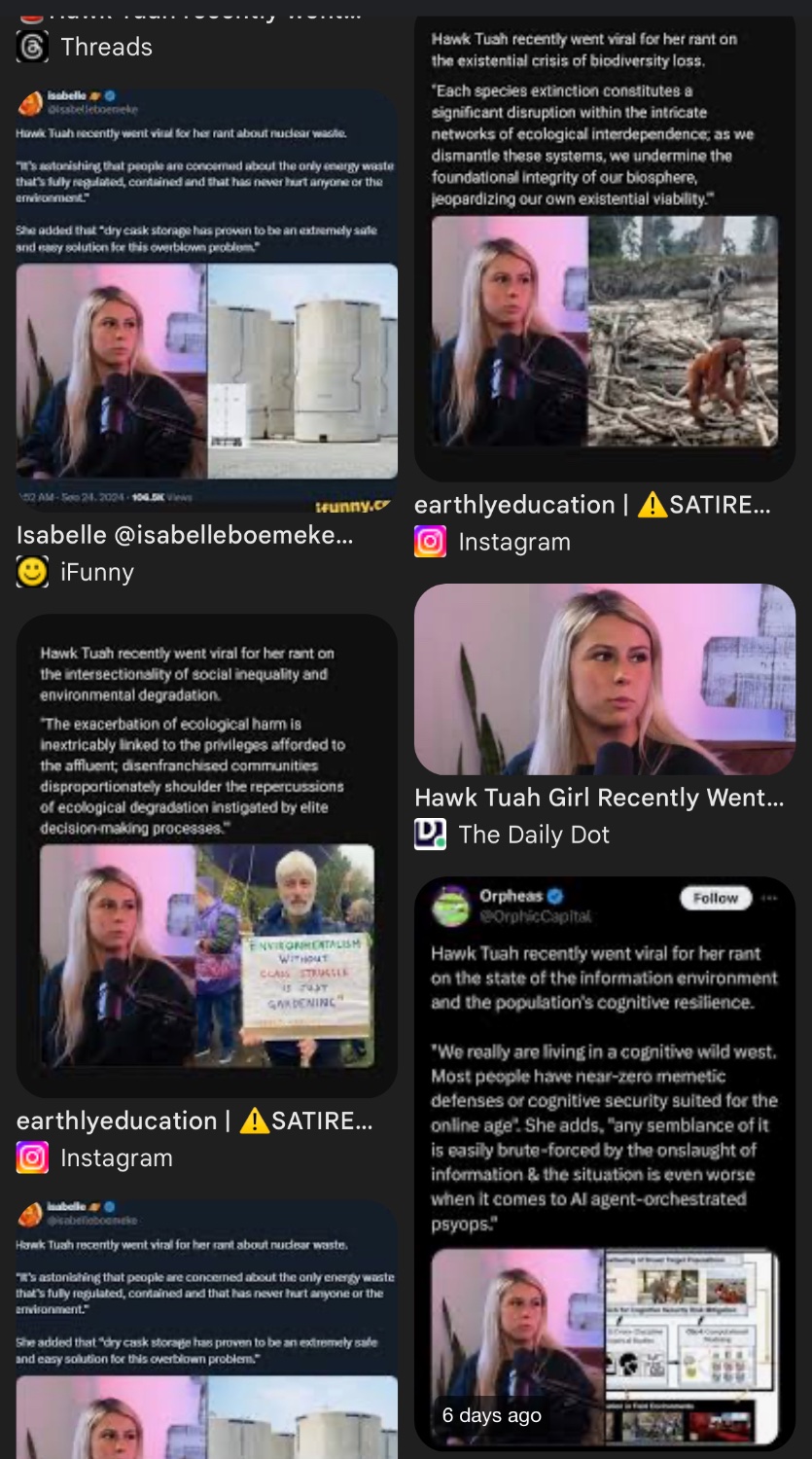
I’m pretty sure that Proton quoting her in the first place is fake. I know she’s milking her 15 minutes of fame for all she can, but this seems outside her experience.
but this seems outside her experience.
When has that ever stopped people from saying shit.
I have a vpn for… reasons… 🏴☠️⚓️🏴☠️
I have VPN so I can look at porn.
I just wanna look at me Japanese cartoons
Dude!
why?
Texas ig
Yup, browsing on lemmynsfw is interesting, because redgifs automatically blocks Texas IPs. So it’s a nice handy reminder to enable my VPN, because gifs refuse to load.
Wow, I left the US ten years ago, I had no idea it had got this bad. You need a VPN to browse porn? :(
It depends on your state. There’s a handful that passed laws requiring porn sites to verify age via ID. Several sites have just outright banned them based on IP as they don’t want to deal with the privacy nightmare.
Then sometimes you’re like me, living in AZ, not even on a VPN, being told “You Texans should be asking for ID” and just wondering how the fuck that’s happening
What’s AZ? Azerbaijan?
Land of the free
Well, the corporations have freedom.
or Utah
deleted by creator
So I’m confused networking stuff has never been my strong suit, is this saying you can still be fucked on public WiFi even if you connect through a VPN?
No, the context is that for many years, shady commercial VPNs would sponsor YouTubers and the scripts they were given were full of lies and half truths about the dangers of public WiFi, with the implication being that if you purchase their VPN service they will “protect you”. But the problems these VPN companies were claiming to solve have already been solved by HTTPS and it’s perfectly fine to use public WiFi without a VPN. They are using scare tactics to sell you a product.
What this poster is saying is that they’re disappointed to see this same fear mongering misinformation from Proton, who have an otherwise good reputation for being consumer friendly.
Exactly. Using a VPN can improve your anonymity, provided you trust your VPN operator more than the infrastructure you’re using. But many VPN vendors claim a VPN is essential to provide security, which isn’t true in the slightest, and Proton shouldn’t be stooping to that level. There are plenty of good reasons to use a VPN that don’t involve illegal activities, but it’s hardly essential for the average person.
no, you can’t have intercourse over the Internet.
Networking stuff IS my strong suit, and I’m confused about what points most people here, including OP, are trying to make here. Maybe I’m just not awake enough yet.
Wtf proton what? What do people think Proton is saying and what’s the WTF part…?
I don’t think the confusion has anything to do with networking. I’ve been puzzling over this post for a few minutes now… To be honest, I think I’m just more confused.
Maybe this is some sort of AI battle of the wits or contagious stroke or something.
Look at the link in the description.
Basically, someone went on a rant saying using public wi-fi w/o a VPN is extremely risky, and Proton is basically boosting it, implying a relationship w/ the OP. Proton argues that this is satire and part of a viral trend of misattributing quotes and topics, and the poster here is calling Proton out on it, likening them to the scammy VPN companies that sponsor YouTube videos and other SM content that oversell their claims.
So basically Proton claims they’re being satirical, and the poster is saying they’re just as bad as other VPN companies.
Yes, to a degree. A VPN protects you from an attacker on the same WiFi network as you and that’s about it.
Most assaults on your privacy don’t happen like that, and for the most part the attacks that do happen like that are stopped by the website using https and proper modern security.
The benefit of the VPN is that it puts some of that protection under your control, but only as far as your VPN provider.A VPN is about as much protection from most cyber attacks as a gun is.
They’re not a security tool, they’re a networking tool. They let you do some network stuff securely, and done correctly they can protect from some things, but the point of them is “this looks like a small, simple LAN, but it’s not”.
It’s much easier to package and sell network tools than security tools, and they’re much more accepted by users, since security tools have a tendency to say “no” a lot, particularly when you might be doing something dumb,and users hate being told no, particularly when they’re doing something dumb.
Exactly. VPN companies vastly oversell what their services offer.
That said, I set up my own VPN, we use one at work, and I’m considering paying for a commercial VPN service. My personal VPN gets around my ISP’s CGNAT so I can host public services within my LAN, my work VPN gives us remote access to protected services, and the commercial VPN I’m considering paying for is to get around my state’s laws (they are requiring ID for porn and social media, and I think that’s a privacy overreach).
VPNs have their place, but they’re hardly “essential” for most people, especially if your concern is security.
is this saying you can still be fucked on public WiFi even if you connect through a VPN?
The quick and dirty answer is no, unless an attacker can figure out a way to get your VPN to strip it’s encryption (doubt you’ll ever see this outside something like defcon but you never know lol).
The long answer is that not all VPNs are equal depending on what you are trying to accomplish.
A VPN will simply tunnel your internet traffic over an encrypted channel to a server anywhere in the world.
On a technical level, this means that it will guarantee your internet traffic is unreadable until it hits the destination, which does mean it can make it more secure to use a public wifi/hotspot.
Of course privacy is actually a massive security iceberg, so some caveats in no particular order are:
spoiler
-
Modern protocols like HTTPS are already encrypted, although someone can still mess with stripping and poisoning techniques, so having a VPN running would be peace of mind.
-
Your privacy from companies like Google, Facebook, etc won’t be enforced by a VPN if you don’t also use a new browser session (incognito) because they can easily track your identity via cookies and accounts.
-
Even if you use a fresh session and dedicated VPN accounts, aforementioned tech companies can still identify you via statistical modeling based on your activity. They don’t really care what your IP is unless they need to pay tax for a country or follow some random media block law.
-
Your privacy from the government is nonexistent because most VPN companies will share your info if the government requests it.
-
Lots of VPNs choose to block torrenting so they don’t have to deal with protecting their customers (although lots also don’t).
-
Even if you setup your own VPN via a VPS in anonymous way, the government can still watch your exit traffic and link the origin back to you by inspecting the VPN packets (which is why Tor exists, a much different solution to the privacy problem).
You should use a VPN if:
- You want to torrent copyrighted material (yar har piracy)
- You want to spoof your location to get access to geolocked content
- You want to negate an attackers ability to mess with your connections on public WiFi
- You want a secure channel between two of your own locations (make two separate networks accessible to eachother, or VPN to home/work to access resources on that network).
- ^ same thing but remote access etc.
You should not use a VPN if:
- You need to hide what you do on the internet from the government (See Tor, journalists stuck in shithole regimes).
- You want privacy from internet megacorps (you’d have to keep fresh sessions or use them sparingly which you can 90% do without a VPN anyway)
- You want to hide anything after it reaches the VPN server (public VPN services, doesn’t apply if you VPN to something you physically own and access only its local resources).
–
After all that, the use case basically becomes:
- VPN to within your own country to secure your connection on public WiFi
- VPN to home or work to access network
- VPN with a good public service to other countries to watch or torrent media
-
There are some attacks you are vulnerable to on public WiFi that a VPN can help with.
More generally, whoever is transporting your data knows who you are talking to. If you don’t use a VPN, your ISP and whoever owns the router know what websites you are visiting (although they don’t know the specific content). If you use a VPN, your ISP and router know you are using that VPN, but not what websites you are visiting. Now your VPN knows what websites you are visiting, but they still don’t know what the content is.
I hope that helps.
What about using tor instead of a vpn?
You can substitute “Tor” for “VPN” in the above and be largely correct. Tor acts like a VPN, but every packet goes through multiple hops, so an attacker would need to do quite a bit of work (i.e. compromise multiple nodes) to link traffic to you.
So:
- TLS (https) - network owner can’t see specific content, but can determine what sites you visit
- VPN - network owner can’t tell what sites you visit, but can tell you’re on a VPN; VPN can tell what sites you visit, but not specific content
- Tor - network owner can’t tell what sites you visit, but can tell you’re using Tor; Tor exit node operators can see what sites people using it visit, but can’t attribute it to an individual user w/o a sophisticated attack
In most cases, TLS is perfectly fine, provided you make sure to not click through any TLS errors (i.e. certificate can’t be validate => probable middle-man attack), and using a VPN is probably overkill. A VPN protects you from that middle-man attack, but honestly, if you’re savvy enough to use a VPN, you’re probably savvy enough to not get compromised by a middle-man attack. Likewise if you use Tor, you’re probably savvy enough to not get compromised by a middle-man attack.
That said, I fully support using Tor and VPNs, I just won’t go so far as to say someone is dumb for not using them on public Wi-Fi. Make sure you’re connecting to a real Wi-Fi service and don’t disable TLS protections and you’re probably fine, from a security perspective. If you’re likely to be targeted by a government agency, Tor is the bare minimum of what you should use.
Yup. The way I’ve always described it is this:
Http means your employer knows you watched porn on the company WiFi, and they also know which specific videos and what your username for the site is. If site security is particularly lax, they may even know your password.
Https means your employer can see you watched porn on the company WiFi, but they don’t know which video(s) specifically, and they don’t know your login info.
VPN means your employer only knows you connected to a VPN. They may be able to take educated guesses at what type of content you were viewing (streaming video, for example, has a pretty easily identifiable pattern of data transfer,) but they don’t know what video you were watching, or what site it was coming from. The VPN service knows you watched porn, but the aforementioned rules about http and https still apply; If you’re using https, they don’t know specifics.
Tor means even the VPN doesn’t know which specific video(s) you’re watching, because they just see a connection to another Tor node, which sees another tor node, which sees another tor node… Etc. In order to know what you’re watching, they would need to own every node in the chain. If they own both the entry and exit node they may be able to match it to you with a timing attack, (they see packets going into the Tor network at the same time they see packets coming out towards you). Again, they can make educated guesses based on pattern recognition, but they won’t have a clear picture without owning both your entry and exit nodes and performing a timing attack.
Now you can substitute “your employer” for anyone who is trying to get your info. Public WiFi spoofer, your ISP, etc…
Probably worth noting that, if you are using an employer owned system to watch said porn, they likely have software on the endpoint which will let them see what porn you are watching, regardless of HTTPS/VPN/Tor. Depending on how much your employer cares about such things, that may or may not come back to bite you. I’ve worked at places where we regularly reported on users watching porn on work computers, and I’ve worked at places where we only reported on users getting malware while browsing porn at work. But, never assume your activity isn’t being monitored on employer owned systems.
Exactly. If it’s company-issued, assume there’s spyware installed. We recently added a certain level of spyware to ours to monitor system files (afaik it’s not screen recording or anything like that) because these aren’t company issued devices (we bought them separately.
What about DoH/DoT which comes enabled by default in some browsers I believe? This should “hide” your activity from isp/router as well, shouldn’t it?
DoH & DoT still leak the domain name (and of course IP address) you’re connecting to. The domain name leak can be solved by Encrypted Client Hello but that’s still a draft and not turned on for many servers.
The ISP will always know the IP you’re connecting to. Encrypted DNS might get you slightly more privacy for sites using shared IPs like with Cloudflare. But in a lot of cases, there’s only 1 website per IP, so the ISP still knows where you’re browsing. A VPN solves this by routing all traffic through the VPNs IP first. But you can still be tracked just the same by the VPN and to an extent, the VPNs ISP.
Yes and no.
Modern HTTPS connections send the URL you are connecting to in the initial hello, so the remote webserver knows what security certificate to use when you connect. A lot of web servers host multiple sites, especially for smaller webpages, and so it doesn’t assume that since you connected to that specific webserver, that you’re connecting to the site that the webserver is hosting, even if it’s only hosting a single site.
This can leak the data to anyone sniffing the traffic.
You can also determine some traffic by IP address, this is for larger web services like Facebook, youtube and other sites of similar size. They load balance groups of IPs for their traffic, all are serving the same data. So if you connect to an IP that’s owned by Facebook, for example, then your actions can be easily derived.
Since the connection is still secured by TLS, the content can’t be deciphered, but the location you are going to absolutely can.
It really depends on a lot of factors.
Ok, thank you and all the others for explanation.
Yes. X.509 means https is worthless protection from APTs
Edit: its clear from downvotes that people in this community don’t understand security and don’t understand how to use Lemmy downvote buttons
Also - using someone who got famous by describing sucking dick seems quite weird :) Who wants technical advice from her?
What does sucking dick have to do with technical competency?
That’s the joke.
Can someone share proton’s response? I don’t have a xitter account
https://xcancel.com/ProtonVPN you can find it here
Appreciate the alternative!
Grabbed this screenshot because I don’t trust anything on Twitter to stay visible (or the platform to even be stable)
https://protonvpn.com/blog/public-wifi-safety/#:~:text=5 ways to stay safe on public WiFi

Wow, one of a few heroes keeping Nitter alive
Fr
Nobody has a Xitter account.
Millions and millions of idiots do.
Is this some highly-voted pedantry about the site not technically being called “Xitter”? Or wtf is going on in this thread…?
Nobody that matters has a Xitter account*
I thought they were mostly bots and alts
The only effective antivirus program known to man is called a backup
How is this related to a VPN? Antivirus does nothing against a MITM attack.
Woosh
I’m saying that no system is secure on a long enough timeframe . But that if you do get infected you can nuke and pave if you have a backup. Most of these VPN advertisers treat their product VPN like a magic shield / antivirus when it is In fact, nothing more than a fancy condom.
VPN is not an anti-virus program. Also, you can’t really backup your online accounts and restore them in case they are hacked.
I am fully aware it’s not an antivirus program which is why I’m mocking people who pretend that they are. Just being on a virtual private Network does not protect you from man in the middle attacks. Sure it hardens your device against Wi-Fi eavesdropping. But you are still vulnerable to DNS spoofing session hijacking cache poisoning and SSL stripping. Aka a VPN won’t protect you from man in the middle attacks once you’ve entered a site app or network under someone else’s control.
My day job is in web hosting.
When I first saw this I thought it was funny. The fact that so many people are falling for it has only made it even funnier.
FWIW, Haley Welch might seem dumb as bricks, but she also seems quite sweet - doing charity stuff, keeping her other friend from “that” vid for the ride, etc. As far as people becoming famous for bullshit reasons goes, she seems to be handling it well.
Falling for what?
She’s handling fame better than Chappel Roan.
You think she’s not handling fame well because she’s setting clear boundaries, and reminding fans that she’s not their friend just because she’s famous?
No, because she has a reaction video to every single negative thing anyone says on TikTok. I’m all for her boundaries.
she has a reaction video to every single negative thing anyone says on TikTok
Ew.
I feel bad for her, honestly. She was open about her sexuality and she’s conventionally attractive, so now she has all these leering old men on TV slobbering all over her.
Bill Maher practically tried to talk her into bed on his show with his creepy shit about mentoring her.
Oof. What is up with these creepy, sweaty dudes on talkshows? I know they somewhat reflect the general populace, but to pull shit like this on air is just boggling.
They don’t reflect the “general populace” it’s just that you kinda have to be an asshole to become famous or you become an asshole afterwards.
Okay so I haven’t heard about her before this but, from this thread and a quick google search, I feel like I know enough. Anyway. I’m hopeful then that the fame will pass— lots of internet fad celebrities fade and become more or less normal people again soon— but she pockets enough money to live a good life and keep paying it forward.
You know, you’re the first person I’ve seen that’s shared the same view as me (not that I’ve spoken about the topic much! lol)
Woman admits that she has performed an extremely benign sexual act before - ghasp! A girl has given someone a blowjob before!
And more than that, she has a “dumb” accent! Let’s make endless memes about her online basically calling her a slutty moron whose only life skill is sucking cock.
Honestly no wonder women feel pressured to pretend they have no sexual desires
Honestly, I never understand why people like this get the level of fame that they do, but at least stop creeping on the poor lady.
I didn’t know who she was, so I just assumed it was true and that she was just another celebrity sponsored by a VPN company.
Yup, I don’t know who she is, nor do I particularly care. What I do care about is how Proton behaves, and if they’re going to stoop to the levels other VPN providers go to in order to attract customers, it’s not a service I’d like to support.
I’m currently not a Proton customer, but I’ve been considering it. I’m currently w/ Tuta for email and use a DIY VPN, but I could see switching to Proton as their product line expands.
"It’s a prank bro"😅 but seriously as an IT guy I’m tired of pushing VPNs down our (collective) throats, not saying the threat isn’t real but it’s really overblown by the ads
Just free, unregulated market shenanigans.
Better to have ads pushed down our collective throats than let collectivists have us by the throat. An ‘unregulated’ market lets us choose whether or not to use them, instead of justifying their necessity to avoid censorship.
I don’t know how effective VPNs are over a public WiFi network, but I do know it stopped Spectrum from sending me “you are downloading copyrighted material, stop it” emails once I started using one. Fuck Spectrum, I don’t have them anymore, but that seems like a good enough reason to keep using one in certain circumstances.
On public WiFi I just vpn into my home network. The issue with public WiFi is that it can be sniffed by anyone in range since there is generally no encryption.
Although pretty much everything we do is over tls these days, and DoH helps protect against even dns sniffing. There’s still at least some risk to working in the clear over a public WiFi network. At least in information gathering, what bank you use, etc.
But, there’s no real benefit in using a paid vpn over one you own unless you’re downloading illegal content, want to watch another Netflix region, or are in a country with heavy Internet monitoring/filtering.
With TLS and DoH, how is your bank and other information leaked?
Possibly the domain is visible with a traffic monitoring tool. Everything else is between you and the bank via HTTPS. Having said that, whatever is not over https is visible to whoever sits on the same network as yourself.
Importantly, you probably don’t know what all is encrypted in every app you use on your phone, so it’s best practice to encrypt the transport.
He said “which bank”, which could be determined by the sniffing DNS requests, or seeing which IPs his computer is connecting to.
Not a breach of his personal information (assuming the bank that he’s using and the client he’s using after putting everything in TLS properly).
But with DoH you can’t sniff the DNS, that’s the whole point.
But you can see the ip address, which will id the bank. They can derive other information by ip addresses or leaked data and there’s still things using unencrypted connections even today. I generally just connect to my home vpn so at least it’s inly my isp spying on me.
Generally you can also read the SNI.
I think this is one of the things that ech is meant to solve. But ech/esni is still not widespread on smaller sites yet I think.
You actually still can. Have a look at DNS fingerprinting
They need to advertise a legitimate use for their service.
If they don’t have a threat from public wifi or other security concerns to remedy, then the only purpose for their service is to bypass region limits and block infringement notices. They would be considered complicit in such infringement.
That their service also hinders efforts to stop pirates needs to be an “unintended” and “unavoidable” side effect.
There are plenty of legitimate uses for their services, they just aren’t things that the vast majority of people actually need. For example:
- access things in a LAN from a WAN - i.e. access a personal PC when you’re at a friend’s house, and your home LAN is behind CGNAT
- get around local laws - e.g. my state requires ID checks for porn and social media, so getting a VPN one state over gets around that
- prevent ISP from seeing the sites you visit - very valid privacy concern, especially since SNI exists to de-mask TLS packets
There are also some sketchier needs, such as:
- get different content on your streaming platform
- hide sharing of illegal content (i.e. piracy)
- perform illegal transactions (e.g. going on Tor to buy drugs or whatever on the black market)
I think VPNs are trying to appeal to more than just the above needs, they’re trying to create needs to grow their marketshare. That isn’t something a reputable VPN should do, or at least that’s something that would make me hesitate to use a given VPN.
If you want to give an anonymous video to the press or the police. If you don’t hide your ip then it isn’t anonymous and they’ll come question you.
The only thing you need to say is “my ISP uses CGNAT” you can’t host anything or run games for your friends without a way to punch through the CGNAT layer. I mean you could use IPv6 if it weren’t still a joke in the US but here we are.
Yup, CGNAT sucks. But STUN works fine for me, and most games support it, so it’s not a huge issue.
I could pay extra for a public IP, but for the same price I can get a VPS and do other cool stuff, so I just went the WireGuard VPN route. Same end result with a little more latency, but also more flexibility. I host a few static sites directly on the VPS, with everything else going through the VPN, so that’s nice.
get around local laws
That’s not a legitimate use; it’s an illegal use just like piracy is.
especially since SNI exists to de-mask TLS packets
ECH will finally fix this. https://blog.cloudflare.com/encrypted-client-hello/
SNI is still better than what we used to have. Before SNI, every site that used TLS or SSL had to have a dedicated IP address.
That’s not a legitimate use; it’s an illegal use just like piracy is.
My understanding of the law (and yes, I read it) is that it’s not illegal. The law in my state is for service providers to authenticate the ID of any state resident, it’s not a requirement on the resident themselves. The service provider isn’t aware what state I’m a resident of, and state law doesn’t apply outside the state, so I don’t know what law would be violated here.
SNI is still better than what we used to have.
I absolutely agree, and I actually use SNI to route packets for my homelab. Without SNI, I would have to route after handling certificates, which would be annoying because I want TLS to work within my home network, and I mess w/ DNS records to point to my local IPs when inside my network. I could have everything routed through a central hub (so one dedicated machine that handles all TLS), but that’s a single point of failure, and I’m not too happy about that. Or I guess I’d have multiple IPs, and route based on which IP is being hit.
I’ll have to check out ECH. Hopefully I can eat my cake and have it too.
I use Proton when I’m on my university’s campus because they switched to using EDUroam for the campus wifi. I used to be a Sys Admin at a different university a while back, and from what I know, EDUroam allows the IT department to monitor basically all of the traffic over the network. I don’t know exactly how deep that stuff goes, but if I was doing anything personal or sensitive like banking or whatever, I’d flip on the VPN on my personal computer. I also don’t have any personal accounts logged in on the school issued laptop because they have it loaded with institutional spyware. Once I graduate, I’ll blank the drive and reinstall the OS to have a decent Lenovo laptop on hand as a spare.
Edit to add: I use Proton because it was the least shady service that I could get for a reasonable price as a student. It is also helpful for finding textbooks. :)
They can’t decrypt HTTPS unless you installed a certificate controlled by them. The only thing they can know is which domains you visited, but not what you did on it.
They require the certificate to be installed to have access to the network.
I’m not defending Proton. I don’t even use them.
Edit: The region limits thing is nice though. It’s not why I got the VPN, but it’s nice to not have to pay to watch the Olympics and just watch it via the CBC or the BBC.
I experienced the same with Cox Internet.
All ISPs are legally obligated to forward that shit to you. The alerts are not from spectrum, they’re just relaying the information.
Right now, copyright owners do not have legal permission to find out who you are directly without a court order. They would only seek that information if they were planning to file a lawsuit.
Media companies know, from the Napster incident, that such actions can backfire stupendously. It’s rare that they even bother anymore. I can go into detail on why, but I’ll leave it out for brevity.
So they send the notice to your ISP, who is legally obligated to match the information on the notice to the subscriber and forward the notice to you.
For many, this goes to an ISP provided mailbox, which most people ignore the existence of it. Clearly spectrum operates differently.
The notices are from copyright holders who have no idea who you are, and can’t determine that information unless they intend to sue you. So those can be, for the most part, ignored.
It’s not your ISPs fault that you got those. They couldn’t give a shit less about what you do on their service, or what you download. They just want you to pay your bill every month and keep the gravy train rolling.
I’m saying fuck Spectrum for other reasons. Either way, there’s less of a trail.
Fair enough. I haven’t used spectrum, so I have no opinion. I’m not in the right country to subscribe to their service, so there’s that.
Have a good day.
Spectrum is a total shit ISP that does shady shit constantly, while being owned by a massive corporation run by a Trump supporter and unfortunately is the only option people have in a lot of places in the U.S.
Anyway, good talk. You have a good day too!
This was poorly executed. The National Park Service twitter account does jokes well.
The only real use case for VPNs is to bypass geo blocking on streaming sites, and the VPN providers know this. They also know that if they lean too hard into that, eventually someone will sue them and their business model will evaporate - so they add the “iT MaKEs yOu mORe SeCurE” nonsense as a fig leaf so they can say with a straight face that they operate a product with legitimate uses
I can’t say VPNs are great for bypassing geo restrictions in 2024, unless you’re talking about tunneling through your home network.
That is definitely what 90% of people use them for.
I think Tom Scott is the only person who’s ever done an honest VPN sponsor read.
Ryan George too, he’s very clear in his VPN ad reads that he uses them to access streaming that isn’t available to him in outer space (his shtick is that he’s an ADstronaut).
Taking cybersecurity advice from someone called Hawk Tuah is modern day version of clicking banner that says find 40+ single women in your zip code
Hot MILFs wanna talk to YOU!
Thank goodness someone explained that to me. I was startong to wonder if she was some sort of technology expert, or something.
Who is she?
the girl from the memes a few weeks ago https://knowyourmeme.com/memes/hawk-tuah-girl
It’s that recent. Jeez. Feels like it’s been a thing for months.
Wait, what day is it? WHAT YEAR IS IT?
OH GOD
you gotta love the “lol joke” fall back. the same strategy used by generation of trolls
Well, I for one wholly believed Hawk Tuah herself endorsed Proton VPN